What Is The File Name Given To The Windows Kernel?
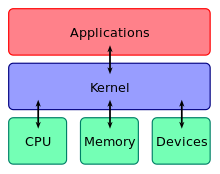
The kernel is a computer program at the cadre of a computer'due south operating system and generally has consummate command over everything in the organisation.[1] Information technology is the portion of the operating arrangement code that is always resident in memory,[2] and facilitates interactions between hardware and software components. A full kernel controls all hardware resources (e.yard. I/O, retention, cryptography) via device drivers, arbitrates conflicts betwixt processes apropos such resources, and optimizes the utilization of common resources e.g. CPU & enshroud usage, file systems, and network sockets. On most systems, the kernel is one of the starting time programs loaded on startup (later the bootloader). It handles the rest of startup also as retentiveness, peripherals, and input/output (I/O) requests from software, translating them into data-processing instructions for the central processing unit.
The critical code of the kernel is usually loaded into a split up area of memory, which is protected from access by awarding software or other less critical parts of the operating system. The kernel performs its tasks, such every bit running processes, managing hardware devices such as the hard disk drive, and handling interrupts, in this protected kernel space. In contrast, awarding programs such as browsers, word processors, or sound or video players use a separate expanse of memory, user space. This separation prevents user data and kernel information from interfering with each other and causing instability and slowness,[1] as well equally preventing malfunctioning applications from affecting other applications or crashing the unabridged operating system. Even in systems where the kernel is included in application address spaces, retentivity protection is used to prevent unauthorized applications from modifying the kernel.
The kernel's interface is a depression-level abstraction layer. When a process requests a service from the kernel, it must invoke a system call, usually through a wrapper function.
There are dissimilar kernel architecture designs. Monolithic kernels run entirely in a unmarried address infinite with the CPU executing in supervisor mode, mainly for speed. Microkernels run near but non all of their services in user space,[3] like user processes do, mainly for resilience and modularity.[4] MINIX iii is a notable example of microkernel design. Instead, the Linux kernel is monolithic, although it is also modular, for information technology can insert and remove loadable kernel modules at runtime.
This key component of a computer system is responsible for executing programs. The kernel takes responsibility for deciding at any time which of the many running programs should be allocated to the processor or processors.
Random-admission memory [edit]
Random-access retention (RAM) is used to store both program instructions and information.[a] Typically, both need to exist present in retentiveness in club for a programme to execute. Often multiple programs will want admission to retentiveness, frequently enervating more retentiveness than the computer has available. The kernel is responsible for deciding which retentiveness each process can use, and determining what to do when not enough retentiveness is available.
Input/output devices [edit]
I/O devices include such peripherals as keyboards, mice, deejay drives, printers, USB devices, network adapters, and display devices. The kernel allocates requests from applications to perform I/O to an appropriate device and provides convenient methods for using the device (typically abstracted to the betoken where the application does non need to know implementation details of the device).
Resource management [edit]
Central aspects necessary in resource direction are defining the execution domain (address infinite) and the protection mechanism used to mediate access to the resources within a domain.[5] Kernels also provide methods for synchronization and inter-process advice (IPC). These implementations may exist located inside the kernel itself or the kernel tin can as well rely on other processes information technology is running. Although the kernel must provide IPC in order to provide access to the facilities provided past each other, kernels must also provide running programs with a method to make requests to access these facilities. The kernel is as well responsible for context switching betwixt processes or threads.
Retentivity management [edit]
The kernel has full access to the system's memory and must allow processes to safely admission this retentiveness as they require information technology. Oft the starting time step in doing this is virtual addressing, usually achieved by paging and/or segmentation. Virtual addressing allows the kernel to make a given concrete address announced to be some other accost, the virtual address. Virtual address spaces may exist different for different processes; the retentivity that ane process accesses at a item (virtual) address may be different retention from what another process accesses at the same address. This allows every program to bear equally if it is the merely one (autonomously from the kernel) running and thus prevents applications from crashing each other.[6]
On many systems, a plan's virtual address may refer to data which is not currently in memory. The layer of indirection provided past virtual addressing allows the operating system to utilize other data stores, like a hard drive, to store what would otherwise have to remain in master retention (RAM). Equally a consequence, operating systems can allow programs to employ more retention than the system has physically available. When a program needs data which is non currently in RAM, the CPU signals to the kernel that this has happened, and the kernel responds by writing the contents of an inactive memory block to disk (if necessary) and replacing information technology with the data requested by the program. The program can and then be resumed from the indicate where it was stopped. This scheme is more often than not known equally demand paging.
Virtual addressing also allows cosmos of virtual partitions of memory in 2 disjointed areas, one existence reserved for the kernel (kernel infinite) and the other for the applications (user space). The applications are not permitted by the processor to accost kernel memory, thus preventing an application from damaging the running kernel. This central partition of retentiveness space has contributed much to the current designs of actual general-purpose kernels and is about universal in such systems, although some research kernels (e.1000., Singularity) take other approaches.
Device direction [edit]
To perform useful functions, processes demand access to the peripherals continued to the computer, which are controlled by the kernel through device drivers. A device driver is a computer programme encapsulating, monitoring and controlling a hardware device (via its Hardware/Software Interface (HSI)) on behalf of the Bone. It provides the operating organisation with an API, procedures and data about how to control and communicate with a certain piece of hardware. Device drivers are an of import and vital dependency for all Os and their applications. The design goal of a commuter is brainchild; the function of the driver is to translate the OS-mandated abstruse part calls (programming calls) into device-specific calls. In theory, a device should work correctly with a suitable driver. Device drivers are used for e.thousand. video cards, sound cards, printers, scanners, modems, and Network cards.
At the hardware level, common abstractions of device drivers include:
- Interfacing straight
- Using a high-level interface (Video BIOS)
- Using a lower-level device driver (file drivers using disk drivers)
- Simulating work with hardware, while doing something entirely different
And at the software level, device driver abstractions include:
- Allowing the operating system directly access to hardware resources
- Only implementing primitives
- Implementing an interface for non-driver software such equally TWAIN
- Implementing a language (frequently a high-level language such as PostScript)
For instance, to show the user something on the screen, an awarding would make a request to the kernel, which would forward the request to its display commuter, which is then responsible for really plotting the character/pixel.[6]
A kernel must maintain a list of available devices. This list may exist known in accelerate (e.g., on an embedded organization where the kernel volition be rewritten if the available hardware changes), configured by the user (typical on older PCs and on systems that are not designed for personal utilise) or detected by the operating organisation at run time (normally called plug and play). In plug-and-play systems, a device manager first performs a browse on different peripheral buses, such as Peripheral Component Interconnect (PCI) or Universal Serial Bus (USB), to detect installed devices, and so searches for the appropriate drivers.
Equally device management is a very OS-specific topic, these drivers are handled differently by each kind of kernel design, merely in every example, the kernel has to provide the I/O to allow drivers to physically access their devices through some port or memory location. Important decisions have to be made when designing the device direction organisation, equally in some designs accesses may involve context switches, making the functioning very CPU-intensive and easily causing a significant performance overhead.[ citation needed ]
Organization calls [edit]
In computing, a system call is how a process requests a service from an operating system's kernel that information technology does not normally take permission to run. System calls provide the interface between a process and the operating organization. Almost operations interacting with the system require permissions not available to a user-level process, e.1000., I/O performed with a device present on the system, or any class of advice with other processes requires the use of organisation calls.
A arrangement call is a mechanism that is used by the application plan to request a service from the operating system. They employ a machine-code instruction that causes the processor to change manner. An instance would be from supervisor style to protected mode. This is where the operating system performs deportment similar accessing hardware devices or the memory management unit of measurement. Generally the operating organization provides a library that sits between the operating system and normal user programs. Usually it is a C library such equally Glibc or Windows API. The library handles the low-level details of passing information to the kernel and switching to supervisor manner. System calls include shut, open up, read, wait and write.
To actually perform useful work, a procedure must be able to admission the services provided by the kernel. This is implemented differently by each kernel, just most provide a C library or an API, which in plough invokes the related kernel functions.[vii]
The method of invoking the kernel role varies from kernel to kernel. If retention isolation is in utilise, it is impossible for a user procedure to phone call the kernel directly, because that would be a violation of the processor's access control rules. A few possibilities are:
- Using a software-simulated interrupt. This method is available on almost hardware, and is therefore very mutual.
- Using a phone call gate. A phone call gate is a special address stored past the kernel in a listing in kernel retentiveness at a location known to the processor. When the processor detects a telephone call to that address, it instead redirects to the target location without causing an access violation. This requires hardware support, but the hardware for it is quite common.
- Using a special system call instruction. This technique requires special hardware support, which common architectures (notably, x86) may lack. System call instructions have been added to recent models of x86 processors, however, and some operating systems for PCs make use of them when available.
- Using a retentiveness-based queue. An application that makes large numbers of requests simply does not need to wait for the outcome of each may add details of requests to an area of retentivity that the kernel periodically scans to discover requests.
Kernel design decisions [edit]
Protection [edit]
An important consideration in the design of a kernel is the support it provides for protection from faults (fault tolerance) and from malicious behaviours (security). These 2 aspects are ordinarily non clearly distinguished, and the adoption of this distinction in the kernel design leads to the rejection of a hierarchical construction for protection.[5]
The mechanisms or policies provided past the kernel can be classified according to several criteria, including: static (enforced at compile time) or dynamic (enforced at run fourth dimension); pre-emptive or post-detection; according to the protection principles they satisfy (e.g., Denning[eight] [ix]); whether they are hardware supported or language based; whether they are more than an open up mechanism or a binding policy; and many more.
Support for hierarchical protection domains[10] is typically implemented using CPU modes.
Many kernels provide implementation of "capabilities", i.due east., objects that are provided to user code which allow limited access to an underlying object managed past the kernel. A common example is file handling: a file is a representation of information stored on a permanent storage device. The kernel may be able to perform many different operations, including read, write, delete or execute, but a user-level application may only be permitted to perform some of these operations (e.yard., it may but be allowed to read the file). A mutual implementation of this is for the kernel to provide an object to the awarding (typically so called a "file handle") which the application may then invoke operations on, the validity of which the kernel checks at the fourth dimension the operation is requested. Such a organisation may be extended to cover all objects that the kernel manages, and indeed to objects provided by other user applications.
An efficient and simple way to provide hardware support of capabilities is to consul to the retentivity management unit (MMU) the responsibleness of checking access-rights for every memory access, a mechanism called capability-based addressing.[11] Well-nigh commercial computer architectures lack such MMU support for capabilities.
An alternative approach is to simulate capabilities using usually supported hierarchical domains. In this approach, each protected object must reside in an address space that the application does non have admission to; the kernel besides maintains a list of capabilities in such memory. When an application needs to access an object protected by a capability, it performs a organization telephone call and the kernel then checks whether the application's adequacy grants information technology permission to perform the requested action, and if it is permitted performs the admission for it (either directly, or by delegating the request to another user-level process). The operation cost of address space switching limits the practicality of this approach in systems with complex interactions between objects, but information technology is used in current operating systems for objects that are not accessed oft or which are not expected to perform rapidly.[12] [13]
If the firmware does not support protection mechanisms, it is possible to simulate protection at a higher level, for example past simulating capabilities past manipulating page tables, but at that place are performance implications.[14] Lack of hardware support may non exist an issue, notwithstanding, for systems that cull to use language-based protection.[15]
An important kernel design decision is the selection of the abstraction levels where the security mechanisms and policies should be implemented. Kernel security mechanisms play a critical office in supporting security at higher levels.[11] [xvi] [17] [18] [19]
Ane approach is to use firmware and kernel support for fault tolerance (see higher up), and build the security policy for malicious behavior on acme of that (adding features such as cryptography mechanisms where necessary), delegating some responsibility to the compiler. Approaches that delegate enforcement of security policy to the compiler and/or the awarding level are often chosen language-based security.
The lack of many critical security mechanisms in electric current mainstream operating systems impedes the implementation of acceptable security policies at the application abstraction level.[sixteen] In fact, a common misconception in computer security is that any security policy can exist implemented in an application regardless of kernel support.[16]
Hardware- or language-based protection [edit]
Typical computer systems today use hardware-enforced rules about what programs are allowed to access what data. The processor monitors the execution and stops a program that violates a rule, such as a user process that tries to write to kernel memory. In systems that lack support for capabilities, processes are isolated from each other past using separate accost spaces.[20] Calls from user processes into the kernel are regulated by requiring them to employ i of the above-described organization call methods.
An alternative arroyo is to use language-based protection. In a language-based protection organisation, the kernel will only allow code to execute that has been produced by a trusted language compiler. The language may then be designed such that it is incommunicable for the developer to instruct it to do something that will violate a security requirement.[15]
Advantages of this approach include:
- No need for separate address spaces. Switching between address spaces is a dull operation that causes a bully bargain of overhead, and a lot of optimization piece of work is currently performed in guild to foreclose unnecessary switches in electric current operating systems. Switching is completely unnecessary in a language-based protection arrangement, as all code can safely operate in the same address space.
- Flexibility. Any protection scheme that can be designed to be expressed via a programming language can exist implemented using this method. Changes to the protection scheme (e.g. from a hierarchical system to a adequacy-based 1) do not require new hardware.
Disadvantages include:
- Longer application startup fourth dimension. Applications must be verified when they are started to ensure they have been compiled by the correct compiler, or may need recompiling either from source code or from bytecode.
- Inflexible type systems. On traditional systems, applications frequently perform operations that are not type prophylactic. Such operations cannot be permitted in a language-based protection system, which means that applications may need to be rewritten and may, in some cases, lose performance.
Examples of systems with language-based protection include JX and Microsoft's Singularity.
Procedure cooperation [edit]
Edsger Dijkstra proved that from a logical point of view, atomic lock and unlock operations operating on binary semaphores are sufficient primitives to express whatever functionality of procedure cooperation.[21] Even so this approach is mostly held to be lacking in terms of prophylactic and efficiency, whereas a bulletin passing arroyo is more flexible.[22] A number of other approaches (either lower- or higher-level) are available as well, with many modern kernels providing support for systems such as shared memory and remote procedure calls.
I/O device management [edit]
The idea of a kernel where I/O devices are handled uniformly with other processes, as parallel co-operating processes, was first proposed and implemented by Brinch Hansen (although like ideas were suggested in 1967[23] [24]). In Hansen'due south description of this, the "common" processes are called internal processes, while the I/O devices are chosen external processes.[22]
Like to physical memory, assuasive applications directly admission to controller ports and registers tin crusade the controller to malfunction, or arrangement to crash. With this, depending on the complexity of the device, some devices can get surprisingly complex to program, and use several different controllers. Because of this, providing a more abstract interface to manage the device is important. This interface is normally washed past a device driver or hardware abstraction layer. Ofttimes, applications will require admission to these devices. The kernel must maintain the list of these devices past querying the system for them in some way. This can be done through the BIOS, or through ane of the diverse system buses (such every bit PCI/PCIE, or USB). Using an case of a video driver, when an application requests an operation on a device, such every bit displaying a grapheme, the kernel needs to send this request to the current agile video driver. The video commuter, in turn, needs to carry out this request. This is an example of inter-process communication (IPC).
Kernel-wide design approaches [edit]
Naturally, the above listed tasks and features can exist provided in many means that differ from each other in design and implementation.
The principle of separation of mechanism and policy is the substantial difference between the philosophy of micro and monolithic kernels.[25] [26] Here a mechanism is the support that allows the implementation of many different policies, while a policy is a particular "mode of operation". Example:
- Mechanism: User login attempts are routed to an authorization server
- Policy: Authorization server requires a countersign which is verified against stored passwords in a database
Because the machinery and policy are separated, the policy can be hands changed to e.k. require the use of a security token.
In minimal microkernel just some very basic policies are included,[26] and its mechanisms allows what is running on top of the kernel (the remaining part of the operating arrangement and the other applications) to decide which policies to adopt (as retention management, high level process scheduling, file organization direction, etc.).[five] [22] A monolithic kernel instead tends to include many policies, therefore restricting the remainder of the arrangement to rely on them.
Per Brinch Hansen presented arguments in favour of separation of mechanism and policy.[5] [22] The failure to properly fulfill this separation is one of the major causes of the lack of substantial innovation in existing operating systems,[five] a problem mutual in computer architecture.[27] [28] [29] The monolithic design is induced by the "kernel manner"/"user mode" architectural approach to protection (technically called hierarchical protection domains), which is common in conventional commercial systems;[30] in fact, every module needing protection is therefore preferably included into the kernel.[30] This link between monolithic pattern and "privileged way" can exist reconducted to the key issue of mechanism-policy separation;[v] in fact the "privileged mode" architectural approach melds together the protection mechanism with the security policies, while the major alternative architectural approach, capability-based addressing, clearly distinguishes between the two, leading naturally to a microkernel design[5] (see Separation of protection and security).
While monolithic kernels execute all of their code in the same address space (kernel space), microkernels try to run most of their services in user space, aiming to improve maintainability and modularity of the codebase.[iv] Most kernels do not fit exactly into ane of these categories, only are rather institute in betwixt these two designs. These are called hybrid kernels. More exotic designs such as nanokernels and exokernels are available, but are seldom used for production systems. The Xen hypervisor, for example, is an exokernel.
Monolithic kernels [edit]

Diagram of a monolithic kernel
In a monolithic kernel, all OS services run along with the main kernel thread, thus also residing in the same memory surface area. This approach provides rich and powerful hardware admission. Some developers, such as UNIX developer Ken Thompson, maintain that information technology is "easier to implement a monolithic kernel"[31] than microkernels. The main disadvantages of monolithic kernels are the dependencies betwixt system components – a bug in a device commuter might crash the entire system – and the fact that big kernels can go very difficult to maintain.
Monolithic kernels, which have traditionally been used past Unix-like operating systems, contain all the operating arrangement core functions and the device drivers. This is the traditional design of UNIX systems. A monolithic kernel is one single programme that contains all of the code necessary to perform every kernel-related chore. Every office which is to exist accessed past most programs which cannot be put in a library is in the kernel space: Device drivers, scheduler, memory handling, file systems, and network stacks. Many organisation calls are provided to applications, to allow them to access all those services. A monolithic kernel, while initially loaded with subsystems that may not exist needed, can be tuned to a point where it is as fast equally or faster than the one that was specifically designed for the hardware, although more relevant in a general sense. Modernistic monolithic kernels, such as those of Linux (one of the kernels of the GNU operating system) and FreeBSD kernel, both of which fall into the category of Unix-like operating systems, characteristic the ability to load modules at runtime, thereby assuasive easy extension of the kernel'due south capabilities as required, while helping to minimize the amount of code running in kernel space. In the monolithic kernel, some advantages hinge on these points:
- Since at that place is less software involved information technology is faster.
- Equally it is one single slice of software it should be smaller both in source and compiled forms.
- Less code generally means fewer bugs which can translate to fewer security problems.
Near piece of work in the monolithic kernel is done via system calls. These are interfaces, commonly kept in a tabular structure, that admission some subsystem within the kernel such as disk operations. Essentially calls are fabricated within programs and a checked copy of the asking is passed through the system phone call. Hence, not far to travel at all. The monolithic Linux kernel can be made extremely small not only because of its power to dynamically load modules but also because of its ease of customization. In fact, there are some versions that are small-scale enough to fit together with a large number of utilities and other programs on a unmarried floppy disk and still provide a fully functional operating system (ane of the most popular of which is muLinux). This ability to miniaturize its kernel has also led to a rapid growth in the use of Linux in embedded systems.
These types of kernels consist of the cadre functions of the operating system and the device drivers with the power to load modules at runtime. They provide rich and powerful abstractions of the underlying hardware. They provide a small set up of simple hardware abstractions and employ applications chosen servers to provide more functionality. This item approach defines a high-level virtual interface over the hardware, with a ready of system calls to implement operating organisation services such as process direction, concurrency and memory management in several modules that run in supervisor mode. This design has several flaws and limitations:
- Coding in kernel tin can be challenging, in part considering one cannot utilise mutual libraries (like a full-featured libc), and because 1 needs to use a source-level debugger like gdb. Rebooting the computer is frequently required. This is not just a problem of convenience to the developers. When debugging is harder, and every bit difficulties go stronger, information technology becomes more likely that lawmaking will exist "buggier".
- Bugs in one part of the kernel have potent side furnishings; since every part in the kernel has all the privileges, a problems in one office can corrupt data construction of another, totally unrelated office of the kernel, or of whatsoever running programme.
- Kernels often become very large and difficult to maintain.
- Even if the modules servicing these operations are split up from the whole, the code integration is tight and difficult to do correctly.
- Since the modules run in the same address space, a problems can bring down the unabridged system.
- Monolithic kernels are not portable; therefore, they must exist rewritten for each new architecture that the operating system is to be used on.
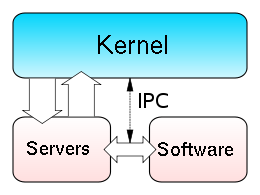
In the microkernel approach, the kernel itself just provides basic functionality that allows the execution of servers, separate programs that presume former kernel functions, such as device drivers, GUI servers, etc.
Examples of monolithic kernels are AIX kernel, HP-UX kernel and Solaris kernel.
Microkernels [edit]
Microkernel (also abbreviated μK or uK) is the term describing an arroyo to operating organization design by which the functionality of the system is moved out of the traditional "kernel", into a set of "servers" that communicate through a "minimal" kernel, leaving as little as possible in "system space" and every bit much equally possible in "user space". A microkernel that is designed for a specific platform or device is but e'er going to have what information technology needs to operate. The microkernel approach consists of defining a simple abstraction over the hardware, with a set of primitives or system calls to implement minimal Os services such every bit memory management, multitasking, and inter-process advice. Other services, including those normally provided by the kernel, such as networking, are implemented in user-infinite programs, referred to as servers. Microkernels are easier to maintain than monolithic kernels, only the large number of system calls and context switches might slow down the organisation because they typically generate more than overhead than plain function calls.
But parts which really require being in a privileged style are in kernel infinite: IPC (Inter-Process Communication), bones scheduler, or scheduling primitives, bones memory handling, basic I/O primitives. Many critical parts are now running in user space: The consummate scheduler, memory handling, file systems, and network stacks. Micro kernels were invented equally a reaction to traditional "monolithic" kernel design, whereby all organisation functionality was put in a ane static program running in a special "system" mode of the processor. In the microkernel, but the well-nigh fundamental of tasks are performed such as being able to access some (not necessarily all) of the hardware, manage memory and coordinate message passing between the processes. Some systems that employ micro kernels are QNX and the HURD. In the case of QNX and Hurd user sessions can be unabridged snapshots of the system itself or views as it is referred to. The very essence of the microkernel architecture illustrates some of its advantages:
- Easier to maintain
- Patches can be tested in a dissever instance, and then swapped in to accept over a production instance.
- Rapid development fourth dimension and new software can exist tested without having to reboot the kernel.
- More than persistence in full general, if ane instance goes haywire, information technology is often possible to substitute it with an operational mirror.
Most microkernels apply a bulletin passing system to handle requests from ane server to another. The message passing system generally operates on a port basis with the microkernel. Every bit an example, if a asking for more memory is sent, a port is opened with the microkernel and the request sent through. Once inside the microkernel, the steps are like to system calls. The rationale was that it would bring modularity in the system architecture, which would entail a cleaner system, easier to debug or dynamically modify, customizable to users' needs, and more performing. They are part of the operating systems like GNU Hurd, MINIX, MkLinux, QNX and Redox Bone. Although microkernels are very small by themselves, in combination with all their required auxiliary code they are, in fact, frequently larger than monolithic kernels. Advocates of monolithic kernels also point out that the ii-tiered structure of microkernel systems, in which most of the operating system does not interact directly with the hardware, creates a not-insignificant cost in terms of system efficiency. These types of kernels normally provide simply the minimal services such as defining memory accost spaces, inter-process communication (IPC) and the process management. The other functions such as running the hardware processes are not handled direct past microkernels. Proponents of micro kernels bespeak out those monolithic kernels have the disadvantage that an fault in the kernel can cause the unabridged system to crash. However, with a microkernel, if a kernel procedure crashes, it is nonetheless possible to forbid a crash of the system as a whole by merely restarting the service that caused the error.
Other services provided by the kernel such as networking are implemented in user-space programs referred to as servers. Servers let the operating system to exist modified past simply starting and stopping programs. For a machine without networking support, for instance, the networking server is not started. The task of moving in and out of the kernel to motion data between the various applications and servers creates overhead which is detrimental to the efficiency of micro kernels in comparison with monolithic kernels.
Disadvantages in the microkernel exist however. Some are:
- Larger running memory footprint
- More software for interfacing is required, there is a potential for operation loss.
- Messaging bugs tin be harder to set up due to the longer trip they accept to take versus the one off copy in a monolithic kernel.
- Process management in full general can be very complicated.
The disadvantages for microkernels are extremely context-based. As an example, they work well for small single-purpose (and disquisitional) systems because if not many processes demand to run, and then the complications of procedure management are effectively mitigated.
A microkernel allows the implementation of the remaining role of the operating organization as a normal application programme written in a high-level language, and the use of different operating systems on acme of the same unchanged kernel. It is as well possible to dynamically switch among operating systems and to have more than 1 active simultaneously.[22]
Monolithic kernels vs. microkernels [edit]
As the computer kernel grows, so grows the size and vulnerability of its trusted calculating base; and, besides reducing security, there is the problem of enlarging the memory footprint. This is mitigated to some caste by perfecting the virtual retentiveness system, but not all reckoner architectures have virtual retention support.[32] To reduce the kernel's footprint, extensive editing has to exist performed to carefully remove unneeded code, which tin be very difficult with non-obvious interdependencies between parts of a kernel with millions of lines of lawmaking.
By the early 1990s, due to the various shortcomings of monolithic kernels versus microkernels, monolithic kernels were considered obsolete by most all operating organization researchers.[ citation needed ] As a upshot, the pattern of Linux as a monolithic kernel rather than a microkernel was the topic of a famous fence between Linus Torvalds and Andrew Tanenbaum.[33] There is merit on both sides of the argument presented in the Tanenbaum–Torvalds debate.
Functioning [edit]
Monolithic kernels are designed to have all of their lawmaking in the same address space (kernel space), which some developers argue is necessary to increase the performance of the system.[34] Some developers too maintain that monolithic systems are extremely efficient if well written.[34] The monolithic model tends to be more than efficient[35] through the utilise of shared kernel memory, rather than the slower IPC system of microkernel designs, which is typically based on message passing.[ citation needed ]
The performance of microkernels was poor in both the 1980s and early 1990s.[36] [37] Even so, studies that empirically measured the operation of these microkernels did not clarify the reasons of such inefficiency.[36] The explanations of this data were left to "folklore", with the assumption that they were due to the increased frequency of switches from "kernel-fashion" to "user-mode", to the increased frequency of inter-procedure communication and to the increased frequency of context switches.[36]
In fact, as guessed in 1995, the reasons for the poor performance of microkernels might every bit well accept been: (1) an actual inefficiency of the whole microkernel approach, (2) the item concepts implemented in those microkernels, and (iii) the item implementation of those concepts. Therefore it remained to be studied if the solution to build an efficient microkernel was, different previous attempts, to apply the correct construction techniques.[36]
On the other end, the hierarchical protection domains architecture that leads to the pattern of a monolithic kernel[30] has a significant performance drawback each time there'south an interaction between different levels of protection (i.e., when a procedure has to manipulate a data structure both in "user way" and "supervisor mode"), since this requires message copying by value.[38]

The hybrid kernel approach combines the speed and simpler blueprint of a monolithic kernel with the modularity and execution safety of a microkernel
Hybrid (or modular) kernels [edit]
Hybrid kernels are used in well-nigh commercial operating systems such equally Microsoft Windows NT 3.1, NT 3.5, NT iii.51, NT iv.0, 2000, XP, Vista, vii, 8, 8.1 and ten. Apple Inc's own macOS uses a hybrid kernel called XNU which is based upon code from OSF/1's Mach kernel (OSFMK 7.three)[39] and FreeBSD's monolithic kernel. They are like to micro kernels, except they include some additional code in kernel-infinite to increase functioning. These kernels represent a compromise that was implemented by some developers to accommodate the major advantages of both monolithic and micro kernels. These types of kernels are extensions of micro kernels with some properties of monolithic kernels. Unlike monolithic kernels, these types of kernels are unable to load modules at runtime on their own. Hybrid kernels are micro kernels that have some "non-essential" code in kernel-infinite in order for the code to run more quickly than information technology would were information technology to be in user-space. Hybrid kernels are a compromise between the monolithic and microkernel designs. This implies running some services (such as the network stack or the filesystem) in kernel infinite to reduce the performance overhead of a traditional microkernel, but all the same running kernel code (such every bit device drivers) equally servers in user infinite.
Many traditionally monolithic kernels are now at to the lowest degree adding (or else using) the module capability. The nigh well known of these kernels is the Linux kernel. The modular kernel essentially tin can have parts of it that are congenital into the core kernel binary or binaries that load into retentivity on demand. Information technology is important to note that a code tainted module has the potential to destabilize a running kernel. Many people go confused on this point when discussing micro kernels. It is possible to write a driver for a microkernel in a completely split up retentivity space and examination it before "going" live. When a kernel module is loaded, it accesses the monolithic portion's memory space by adding to it what it needs, therefore, opening the doorway to possible pollution. A few advantages to the modular (or) Hybrid kernel are:
- Faster development time for drivers that can operate from within modules. No reboot required for testing (provided the kernel is not destabilized).
- On demand capability versus spending time recompiling a whole kernel for things similar new drivers or subsystems.
- Faster integration of third party technology (related to development simply pertinent unto itself withal).
Modules, more often than not, communicate with the kernel using a module interface of some sort. The interface is generalized (although item to a given operating organisation) and then information technology is not always possible to utilise modules. Oft the device drivers may need more flexibility than the module interface affords. Substantially, it is two system calls and often the prophylactic checks that only take to be done once in the monolithic kernel at present may be washed twice. Some of the disadvantages of the modular arroyo are:
- With more interfaces to pass through, the possibility of increased bugs exists (which implies more security holes).
- Maintaining modules tin be confusing for some administrators when dealing with bug like symbol differences.
Nanokernels [edit]
A nanokernel delegates virtually all services – including even the about basic ones like interrupt controllers or the timer – to device drivers to make the kernel memory requirement even smaller than a traditional microkernel.[40]
Exokernels [edit]
Exokernels are a all the same-experimental arroyo to operating system design. They differ from other types of kernels in limiting their functionality to the protection and multiplexing of the raw hardware, providing no hardware abstractions on top of which to develop applications. This separation of hardware protection from hardware management enables application developers to make up one's mind how to brand the about efficient utilize of the available hardware for each specific programme.
Exokernels in themselves are extremely small. Notwithstanding, they are accompanied by library operating systems (see also unikernel), providing application developers with the functionalities of a conventional operating organisation. This comes down to every user writing his own remainder-of-the kernel from near scratch, which is a very-risky, complex and quite a daunting assignment - specially in a time-constrained production-oriented environment, which is why exokernels have never caught on.[ citation needed ] A major advantage of exokernel-based systems is that they can incorporate multiple library operating systems, each exporting a different API, for example one for high level UI development and one for real-time control.
History of kernel development [edit]
Early operating arrangement kernels [edit]
Strictly speaking, an operating organisation (and thus, a kernel) is not required to run a figurer. Programs tin be directly loaded and executed on the "blank metal" automobile, provided that the authors of those programs are willing to work without any hardware brainchild or operating system support. Virtually early computers operated this way during the 1950s and early 1960s, which were reset and reloaded between the execution of different programs. Eventually, small ancillary programs such as program loaders and debuggers were left in retentivity between runs, or loaded from ROM. As these were developed, they formed the basis of what became early operating system kernels. The "blank metallic" arroyo is nevertheless used today on some video game consoles and embedded systems,[41] merely in general, newer computers use modern operating systems and kernels.
In 1969, the RC 4000 Multiprogramming System introduced the system design philosophy of a pocket-sized nucleus "upon which operating systems for different purposes could be congenital in an orderly manner",[42] what would exist called the microkernel approach.
Time-sharing operating systems [edit]
In the decade preceding Unix, computers had grown enormously in ability – to the point where computer operators were looking for new ways to get people to use their spare fourth dimension on their machines. One of the major developments during this era was time-sharing, whereby a number of users would get small slices of computer time, at a rate at which it appeared they were each continued to their own, slower, car.[43]
The development of fourth dimension-sharing systems led to a number of problems. One was that users, especially at universities where the systems were being adult, seemed to want to hack the system to get more CPU time. For this reason, security and access control became a major focus of the Multics projection in 1965.[44] Another ongoing issue was properly handling computing resources: users spent virtually of their time staring at the terminal and thinking most what to input instead of really using the resources of the computer, and a time-sharing organization should give the CPU time to an active user during these periods. Finally, the systems typically offered a memory bureaucracy several layers deep, and partitioning this expensive resource led to major developments in virtual memory systems.
Amiga [edit]
The Commodore Amiga was released in 1985, and was among the showtime – and certainly nigh successful – home computers to feature an avant-garde kernel architecture. The AmigaOS kernel's executive component, exec.library, uses a microkernel message-passing design, but at that place are other kernel components, like graphics.library, that have direct admission to the hardware. At that place is no memory protection, and the kernel is about ever running in user manner. Simply special actions are executed in kernel mode, and user-mode applications can ask the operating system to execute their code in kernel manner.
Unix [edit]
A diagram of the predecessor/successor family relationship for Unix-like systems
During the blueprint phase of Unix, programmers decided to model every high-level device as a file, considering they believed the purpose of computation was data transformation.[45]
For example, printers were represented as a "file" at a known location – when data was copied to the file, information technology printed out. Other systems, to provide a similar functionality, tended to virtualize devices at a lower level – that is, both devices and files would exist instances of some lower level concept. Virtualizing the organization at the file level allowed users to manipulate the unabridged system using their existing file management utilities and concepts, dramatically simplifying functioning. Equally an extension of the same paradigm, Unix allows programmers to dispense files using a series of small programs, using the concept of pipes, which allowed users to complete operations in stages, feeding a file through a chain of single-purpose tools. Although the stop event was the same, using smaller programs in this manner dramatically increased flexibility besides as ease of evolution and use, assuasive the user to modify their workflow by adding or removing a program from the chain.
In the Unix model, the operating organisation consists of two parts: first, the huge collection of utility programs that drive most operations; second, the kernel that runs the programs.[45] Under Unix, from a programming standpoint, the distinction between the two is adequately sparse; the kernel is a program, running in supervisor mode,[46] that acts as a programme loader and supervisor for the pocket-sized utility programs making up the rest of the arrangement, and to provide locking and I/O services for these programs; beyond that, the kernel didn't intervene at all in user space.
Over the years the computing model changed, and Unix'due south treatment of everything as a file or byte stream no longer was every bit universally applicative equally information technology was before. Although a terminal could exist treated every bit a file or a byte stream, which is printed to or read from, the same did non seem to be truthful for a graphical user interface. Networking posed another problem. Even if network communication can be compared to file access, the low-level packet-oriented compages dealt with discrete chunks of data and non with whole files. As the capability of computers grew, Unix became increasingly cluttered with lawmaking. It is likewise because the modularity of the Unix kernel is extensively scalable.[47] While kernels might take had 100,000 lines of code in the seventies and eighties, kernels similar Linux, of modern Unix successors similar GNU, accept more than 13 million lines.[48]
Modern Unix-derivatives are by and large based on module-loading monolithic kernels. Examples of this are the Linux kernel in the many distributions of GNU, IBM AIX, equally well as the Berkeley Software Distribution variant kernels such equally FreeBSD, DragonflyBSD, OpenBSD, NetBSD, and macOS. Autonomously from these alternatives, amateur developers maintain an active operating system development community, populated past cocky-written hobby kernels which mostly end upward sharing many features with Linux, FreeBSD, DragonflyBSD, OpenBSD or NetBSD kernels and/or beingness compatible with them.[49]
Mac Os [edit]
Apple starting time launched its classic Mac Os in 1984, bundled with its Macintosh personal computer. Apple moved to a nanokernel design in Mac OS eight.vi. Against this, the modern macOS (originally named Mac Os X) is based on Darwin, which uses a hybrid kernel called XNU, which was created by combining the iv.3BSD kernel and the Mach kernel.[50]
Microsoft Windows [edit]
Microsoft Windows was start released in 1985 equally an add-on to MS-DOS. Considering of its dependence on another operating organization, initial releases of Windows, prior to Windows 95, were considered an operating environment (non to exist confused with an operating system). This production line connected to evolve through the 1980s and 1990s, with the Windows 9x series adding 32-scrap addressing and pre-emptive multitasking; only concluded with the release of Windows Me in 2000.
Microsoft also developed Windows NT, an operating organization with a very similar interface, but intended for high-finish and business users. This line started with the release of Windows NT 3.ane in 1993, and was introduced to full general users with the release of Windows XP in October 2001—replacing Windows 9x with a completely unlike, much more sophisticated operating organization. This is the line that continues with Windows 11.
The architecture of Windows NT's kernel is considered a hybrid kernel because the kernel itself contains tasks such equally the Window Manager and the IPC Managers, with a customer/server layered subsystem model.[51] It was designed equally a modified microkernel, as the Windows NT kernel was influenced past the Mach microkernel but does non meet all of the criteria of a pure microkernel.
IBM Supervisor [edit]
Supervisory program or supervisor is a estimator program, usually part of an operating organization, that controls the execution of other routines and regulates work scheduling, input/output operations, error actions, and like functions and regulates the menstruation of piece of work in a data processing system.
Historically, this term was essentially associated with IBM'south line of mainframe operating systems starting with Os/360. In other operating systems, the supervisor is generally called the kernel.
In the 1970s, IBM further abstracted the supervisor state from the hardware, resulting in a hypervisor that enabled total virtualization, i.eastward. the capacity to run multiple operating systems on the same automobile totally independently from each other. Hence the outset such organisation was called Virtual Machine or VM.
Development of microkernels [edit]
Although Mach, developed by Richard Rashid at Carnegie Mellon University, is the all-time-known general-purpose microkernel, other microkernels have been developed with more than specific aims. The L4 microkernel family (mainly the L3 and the L4 kernel) was created to demonstrate that microkernels are not necessarily slow.[52] Newer implementations such as Fiasco and Pistachio are able to run Linux next to other L4 processes in carve up accost spaces.[53] [54]
Additionally, QNX is a microkernel which is principally used in embedded systems,[55] and the open-source software MINIX, while originally created for educational purposes, is at present focused on being a highly reliable and self-healing microkernel OS.
See as well [edit]
- Comparison of operating organisation kernels
- Inter-process communication
- Operating system
- Virtual memory
Notes [edit]
- ^ It may depend on the Computer architecture
References [edit]
- ^ a b "Kernel". Linfo. Bellevue Linux Users Grouping. Archived from the original on viii Dec 2006. Retrieved 15 September 2016.
- ^ Randal East. Bryant; David R. O'Hallaron (2016). Computer Systems: A Programmer'south Perspective (Third ed.). Pearson. p. 17. ISBN978-0134092669.
- ^ cf. Daemon (computing)
- ^ a b Roch 2004
- ^ a b c d due east f g Wulf 1974 pp.337–345
- ^ a b Silberschatz 1991
- ^ Tanenbaum, Andrew S. (2008). Modern Operating Systems (3rd ed.). Prentice Hall. pp. fifty–51. ISBN978-0-xiii-600663-3.
. . . nearly all system calls [are] invoked from C programs past calling a library procedure . . . The library procedure . . . executes a TRAP educational activity to switch from user mode to kernel mode and start execution . . .
- ^ Denning 1976
- ^ Swift 2005, p.29 quote: "isolation, resources control, decision verification (checking), and error recovery."
- ^ Schroeder 72
- ^ a b Linden 76
- ^ Stephane Eranian and David Mosberger, Virtual Memory in the IA-64 Linux Kernel Archived 2018-04-03 at the Wayback Machine, Prentice Hall PTR, 2002
- ^ Silberschatz & Galvin, Operating System Concepts, 4th ed, pp. 445 & 446
- ^ Hoch, Charles; J. C. Browne (July 1980). "An implementation of capabilities on the PDP-11/45". ACM SIGOPS Operating Systems Review. fourteen (3): 22–32. doi:10.1145/850697.850701. S2CID 17487360.
- ^ a b A Language-Based Approach to Security Archived 2018-12-22 at the Wayback Machine, Schneider F., Morrissett G. (Cornell University) and Harper R. (Carnegie Mellon University)
- ^ a b c P. A. Loscocco, S. D. Smalley, P. A. Muckelbauer, R. C. Taylor, S. J. Turner, and J. F. Farrell. The Inevitability of Failure: The Flawed Assumption of Security in Modern Computing Environments Archived 2007-06-21 at the Wayback Machine. In Proceedings of the 21st National Data Systems Security Briefing, pages 303–314, Oct. 1998. [1] Archived 2011-07-21 at the Wayback Motorcar.
- ^ Lepreau, Jay; Ford, Bryan; Hibler, Mike (1996). "The persistent relevance of the local operating system to global applications". Proceedings of the 7th workshop on ACM SIGOPS European workshop Systems support for worldwide applications - EW 7. p. 133. doi:x.1145/504450.504477. S2CID 10027108.
- ^ J. Anderson, Figurer Security Technology Planning Report Archived 2011-07-21 at the Wayback Car, Air Force Elect. Systems Div., ESD-TR-73-51, October 1972.
- ^ Jerry H. Saltzer; Mike D. Schroeder (September 1975). "The protection of information in figurer systems". Proceedings of the IEEE. 63 (nine): 1278–1308. CiteSeerX10.1.1.126.9257. doi:10.1109/PROC.1975.9939. S2CID 269166. Archived from the original on 2021-03-08. Retrieved 2007-07-15 .
- ^ Jonathan S. Shapiro; Jonathan Grand. Smith; David J. Farber (1999). "EROS: a fast capability organisation". Proceedings of the Seventeenth ACM Symposium on Operating Systems Principles. 33 (v): 170–185. doi:x.1145/319344.319163.
- ^ Dijkstra, Eastward. Westward. Cooperating Sequential Processes. Math. Dep., Technological U., Eindhoven, Sept. 1965.
- ^ a b c d e Brinch Hansen lxx pp.238–241
- ^ Harrison, M. C.; Schwartz, J. T. (1967). "SHARER, a time sharing organisation for the CDC 6600". Communications of the ACM. 10 (10): 659–665. doi:ten.1145/363717.363778. S2CID 14550794. Retrieved 2007-01-07 .
- ^ Huxtable, D. H. R.; Warwick, M. T. (1967). Dynamic Supervisors – their design and structure. pp. 11.one–xi.17. doi:10.1145/800001.811675. ISBN9781450373708. S2CID 17709902. Archived from the original on 2020-02-24. Retrieved 2007-01-07 .
- ^ Baiardi 1988
- ^ a b Levin 75
- ^ Denning 1980
- ^ Jürgen Nehmer, "The Immortality of Operating Systems, or: Is Research in Operating Systems all the same Justified?", Lecture Notes In Information science; Vol. 563. Proceedings of the International Workshop on Operating Systems of the 90s and Beyond. pp. 77–83 (1991) ISBN 3-540-54987-0 [two] Archived 2017-03-31 at the Wayback Machine quote: "The by 25 years accept shown that research on operating arrangement compages had a small effect on existing master stream [sic] systems."
- ^ Levy 84, p.1 quote: "Although the complexity of computer applications increases yearly, the underlying hardware architecture for applications has remained unchanged for decades."
- ^ a b c Levy 84, p.one quote: "Conventional architectures back up a single privileged fashion of operation. This structure leads to monolithic design; any module needing protection must be part of the single operating organization kernel. If, instead, whatever module could execute within a protected domain, systems could exist built as a collection of independent modules extensible by any user."
- ^ "Open up Sources: Voices from the Open Source Revolution". 1-56592-582-3. 29 March 1999. Archived from the original on ane Feb 2020. Retrieved 24 March 2019.
- ^ Virtual addressing is most usually achieved through a congenital-in memory management unit.
- ^ Recordings of the debate between Torvalds and Tanenbaum tin exist found at dina.dk Archived 2012-10-03 at the Wayback Auto, groups.google.com Archived 2013-05-26 at the Wayback Auto, oreilly.com Archived 2014-09-21 at the Wayback Machine and Andrew Tanenbaum's website Archived 2015-08-05 at the Wayback Machine
- ^ a b Matthew Russell. "What Is Darwin (and How It Powers Mac OS X)". O'Reilly Media. Archived from the original on 2007-12-08. Retrieved 2008-12-09 . quote: "The tightly coupled nature of a monolithic kernel allows it to make very efficient utilize of the underlying hardware [...] Microkernels, on the other manus, run a lot more of the core processes in userland. [...] Unfortunately, these benefits come up at the toll of the microkernel having to pass a lot of information in and out of the kernel space through a procedure known as a context switch. Context switches introduce considerable overhead and therefore result in a performance penalty."
- ^ "Operating Systems/Kernel Models - Wikiversity". en.wikiversity.org. Archived from the original on 2014-12-eighteen. Retrieved 2014-12-18 .
- ^ a b c d Liedtke 95
- ^ Härtig 97
- ^ Hansen 73, section 7.3 p.233 "interactions betwixt different levels of protection require manual of messages by value"
- ^ Magee, Jim. WWDC 2000 Session 106 – Mac Os X: Kernel. 14 minutes in. Archived from the original on 2021-10-30.
- ^ KeyKOS Nanokernel Architecture Archived 2011-06-21 at the Wayback Machine
- ^ Ball: Embedded Microprocessor Designs, p. 129
- ^ Hansen 2001 (bone), pp.17–xviii
- ^ "BSTJ version of C.ACM Unix paper". bell-labs.com. Archived from the original on 2005-12-30. Retrieved 2006-08-17 .
- ^ Introduction and Overview of the Multics System Archived 2011-07-09 at the Wayback Machine, past F. J. Corbató and V. A. Vissotsky.
- ^ a b "The Single Unix Specification". The open grouping. Archived from the original on 2016-10-04. Retrieved 2016-09-29 .
- ^ The highest privilege level has various names throughout different architectures, such every bit supervisor mode, kernel mode, CPL0, DPL0, ring 0, etc. See Ring (computer security) for more information.
- ^ "Unix's Revenge". asymco.com. 29 September 2010. Archived from the original on 9 November 2010. Retrieved ii October 2010.
- ^ Linux Kernel 2.six: It's Worth More than! Archived 2011-08-21 at WebCite, past David A. Wheeler, October 12, 2004
- ^ This community more often than not gathers at Bona Fide Bone Evolution Archived 2022-01-17 at the Wayback Machine, The Mega-Tokyo Message Board Archived 2022-01-25 at the Wayback Motorcar and other operating system enthusiast spider web sites.
- ^ XNU: The Kernel Archived 2011-08-12 at the Wayback Machine
- ^ "Windows - Official Site for Microsoft Windows 10 Home & Pro Bone, laptops, PCs, tablets & more". windows.com. Archived from the original on 2011-08-20. Retrieved 2019-03-24 .
- ^ "The L4 microkernel family - Overview". os.inf.tu-dresden.de. Archived from the original on 2006-08-21. Retrieved 2006-08-11 .
- ^ "The Fiasco microkernel - Overview". os.inf.tu-dresden.de. Archived from the original on 2006-06-16. Retrieved 2006-07-10 .
- ^ Zoller (inaktiv), Heinz (7 December 2013). "L4Ka - L4Ka Projection". www.l4ka.org. Archived from the original on 19 Apr 2001. Retrieved 24 March 2019.
- ^ "QNX Operating Systems". blackberry.qnx.com. Archived from the original on 2019-03-24. Retrieved 2019-03-24 .
Sources [edit]
- Roch, Benjamin (2004). "Monolithic kernel vs. Microkernel" (PDF). Archived from the original (PDF) on 2006-11-01. Retrieved 2006-ten-12 .
- Silberschatz, Abraham; James 50. Peterson; Peter B. Galvin (1991). Operating system concepts. Boston, Massachusetts: Addison-Wesley. p. 696. ISBN978-0-201-51379-0.
- Ball, Stuart R. (2002) [2002]. Embedded Microprocessor Systems: Real World Designs (get-go ed.). Elsevier Science. ISBN978-0-7506-7534-5.
- Deitel, Harvey M. (1984) [1982]. An introduction to operating systems (revisited offset ed.). Addison-Wesley. p. 673. ISBN978-0-201-14502-1.
- Denning, Peter J. (December 1976). "Fault tolerant operating systems". ACM Computing Surveys. viii (4): 359–389. doi:x.1145/356678.356680. ISSN 0360-0300. S2CID 207736773.
- Denning, Peter J. (April 1980). "Why not innovations in computer compages?". ACM SIGARCH Calculator Architecture News. 8 (ii): 4–7. doi:ten.1145/859504.859506. ISSN 0163-5964. S2CID 14065743.
- Hansen, Per Brinch (April 1970). "The nucleus of a Multiprogramming System". Communications of the ACM. 13 (4): 238–241. CiteSeerX10.ane.1.105.4204. doi:10.1145/362258.362278. ISSN 0001-0782. S2CID 9414037.
- Hansen, Per Brinch (1973). Operating System Principles. Englewood Cliffs: Prentice Hall. p. 496. ISBN978-0-thirteen-637843-3.
- Hansen, Per Brinch (2001). "The evolution of operating systems" (PDF). Archived (PDF) from the original on 2011-07-25. Retrieved 2006-ten-24 . included in book: Per Brinch Hansen, ed. (2001). "1 The evolution of operating systems". Classic operating systems: from batch processing to distributed systems. New York: Springer-Verlag. pp. 1–36. ISBN978-0-387-95113-3.
- Hermann Härtig, Michael Hohmuth, Jochen Liedtke, Sebastian Schönberg, Jean Wolter The performance of μ-kernel-based systems Archived 2020-02-17 at the Wayback Machine, Härtig, Hermann; Hohmuth, Michael; Liedtke, Jochen; Schönberg, Sebastian (1997). "The functioning of μ-kernel-based systems". Proceedings of the sixteenth ACM symposium on Operating systems principles - SOSP '97. p. 66. CiteSeerX10.1.one.56.3314. doi:ten.1145/268998.266660. ISBN978-0897919166. S2CID 1706253. ACM SIGOPS Operating Systems Review, v.31 n.5, p. 66–77, Dec. 1997
- Houdek, M. Due east., Soltis, F. G., and Hoffman, R. L. 1981. IBM System/38 back up for capability-based addressing. In Proceedings of the 8th ACM International Symposium on Estimator Architecture. ACM/IEEE, pp. 341–348.
- Intel Corporation (2002) The IA-32 Architecture Software Programmer's Manual, Volume 1: Bones Architecture
- Levin, R.; Cohen, E.; Corwin, Due west.; Pollack, F.; Wulf, William (1975). "Policy/mechanism separation in Hydra". ACM Symposium on Operating Systems Principles / Proceedings of the Fifth ACM Symposium on Operating Systems Principles. 9 (5): 132–140. doi:x.1145/1067629.806531.
- Levy, Henry Chiliad. (1984). Adequacy-based calculator systems. Maynard, Mass: Digital Printing. ISBN978-0-932376-22-0. Archived from the original on 2007-07-13. Retrieved 2007-07-18 .
- Liedtke, Jochen. On µ-Kernel Construction, Proc. 15th ACM Symposium on Operating Organisation Principles (SOSP), December 1995
- Linden, Theodore A. (December 1976). "Operating Organization Structures to Support Security and Reliable Software". ACM Computing Surveys. 8 (4): 409–445. doi:10.1145/356678.356682. hdl:2027/mdp.39015086560037. ISSN 0360-0300. S2CID 16720589. , "Operating System Structures to Back up Security and Reliable Software" (PDF). Archived (PDF) from the original on 2010-05-28. Retrieved 2010-06-19 .
- Lorin, Harold (1981). Operating systems. Boston, Massachusetts: Addison-Wesley. pp. 161–186. ISBN978-0-201-14464-2.
- Schroeder, Michael D.; Jerome H. Saltzer (March 1972). "A hardware architecture for implementing protection rings". Communications of the ACM. 15 (3): 157–170. CiteSeerX10.1.1.83.8304. doi:ten.1145/361268.361275. ISSN 0001-0782. S2CID 14422402.
- Shaw, Alan C. (1974). The logical pattern of Operating systems. Prentice-Hall. p. 304. ISBN978-0-xiii-540112-v.
- Tanenbaum, Andrew S. (1979). Structured Reckoner Organization. Englewood Cliffs, New Jersey: Prentice-Hall. ISBN978-0-13-148521-1.
- Wulf, Due west.; Eastward. Cohen; Due west. Corwin; A. Jones; R. Levin; C. Pierson; F. Pollack (June 1974). "HYDRA: the kernel of a multiprocessor operating system" (PDF). Communications of the ACM. 17 (vi): 337–345. doi:10.1145/355616.364017. ISSN 0001-0782. S2CID 8011765. Archived from the original (PDF) on 2007-09-26. Retrieved 2007-07-xviii .
- Baiardi, F.; A. Tomasi; M. Vanneschi (1988). Architettura dei Sistemi di Elaborazione, volume 1 (in Italian). Franco Angeli. ISBN978-88-204-2746-vii. Archived from the original on 2012-06-27. Retrieved 2006-ten-x .
- Swift, Michael M.; Brian N. Bershad; Henry M. Levy. Improving the reliability of commodity operating systems (PDF). Archived (PDF) from the original on 2007-07-xix. Retrieved 2007-07-16 .
- Gettys, James; Karlton, Philip L.; McGregor, Scott (1990). "Improving the reliability of commodity operating systems". Software: Practise and Experience. 20: S35–S67. doi:10.1002/spe.4380201404. S2CID 26329062. Retrieved 2010-06-19 .
- Michael 1000. Swift; Brian N. Bershad; Henry 1000. Levy (February 2005). "Improving the reliability of commodity operating systems". ACM Transactions on Computer Systems (TOCS). Clan for Calculating Machinery. 23 (one): 77–110. doi:10.1145/1047915.1047919. eISSN 1557-7333. ISSN 0734-2071. S2CID 208013080.
Further reading [edit]
- Andrew Tanenbaum, Operating Systems – Design and Implementation (3rd edition);
- Andrew Tanenbaum, Mod Operating Systems (Second edition);
- Daniel P. Bovet, Marco Cesati, The Linux Kernel;
- David A. Peterson, Nitin Indurkhya, Patterson, Computer System and Blueprint, Morgan Koffman (ISBN 1-55860-428-6);
- B.Due south. Chalk, Estimator Organisation and Architecture, Macmillan P.(ISBN 0-333-64551-0).
External links [edit]
- Detailed comparison between most popular operating system kernels
What Is The File Name Given To The Windows Kernel?,
Source: https://en.wikipedia.org/wiki/Kernel_(operating_system)
Posted by: chadwickablemplaid.blogspot.com


0 Response to "What Is The File Name Given To The Windows Kernel?"
Post a Comment